
IT for Legal
In a fast-paced world, having reliable and efficient technology solutions is non-negotiable.
Benefits of a MSP
Our comprehensive IT services are designed to streamline your workflow, enhance security, and optimize the overall efficiency of your legal practice.
Industry Expertise
We understand the unique technology challenges faced by legal professionals and have tailored our services to address the specific needs of your legal practice.
Data Security
Robust security measures to protect confidential information, network security, virus protection, encryption and disaster recovery is a necessity.
Scalability
As your practice grows, our IT solutions can scale with you. Whether you’re a solo practitioner or a large law firm, we have the flexibility to meet your evolving needs.
Vendor Management
Colletti Tech manages technology vendor deliverables, support, costs, purchasing, and contracts, saving you time so you can focus on practice.
Streamline Licensing
Colletti Tech has the knowledge to streamline licensing procurement from Adobe or Microsoft 365, to Clio and NetDocuments. We manage your licensing, onboarding users efficiently, provide training and support as your single point of contact for all IT-related vendors.

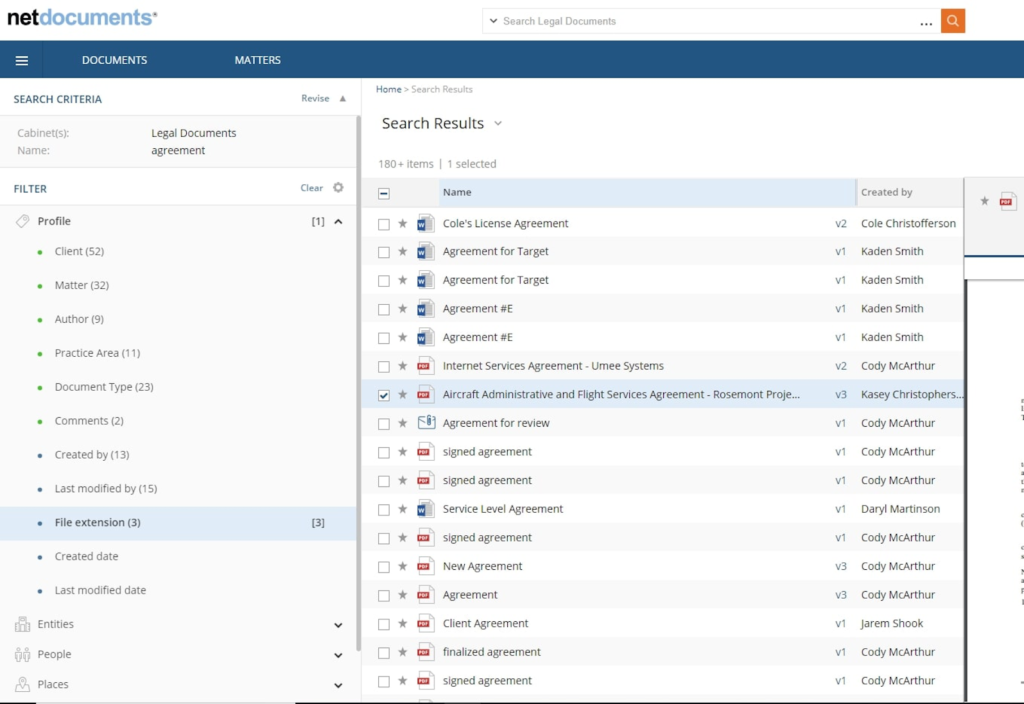
Document Management
Document Management Systems are comprehensive solutions designed to efficiently store, organize, manage, and retrieve legal documents within your firm. We have the expertise to implement a Document Management System, enhancing collaboration, increasing productivity, and empowering your firm.
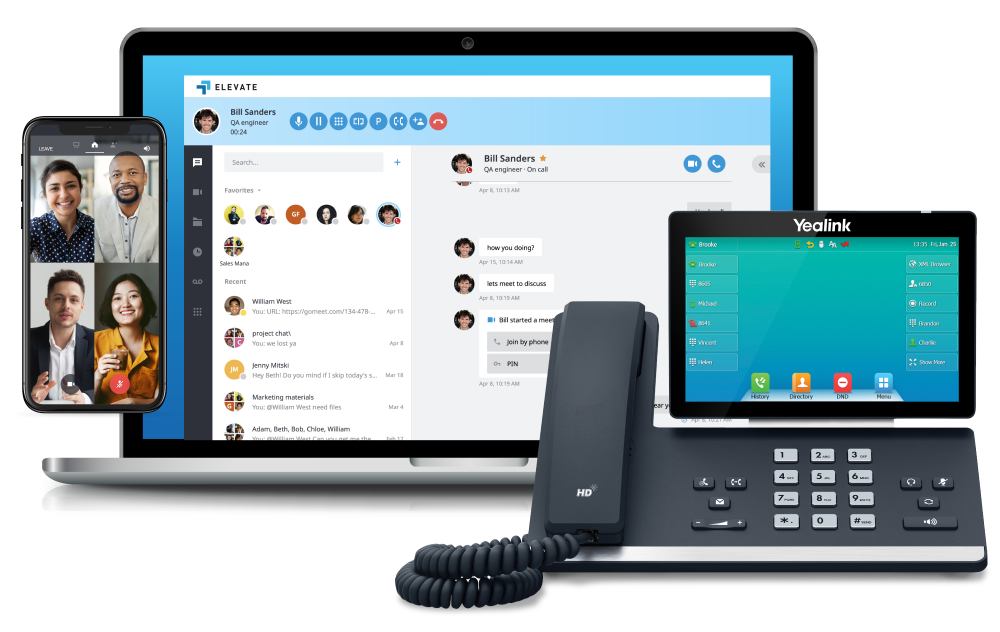
Secure Communications
Anytime, Anywhere
Our platform facilitates real-time calling, messaging, and conferencing among legal professionals. Communicate securely and enhance collaboration from the office, court, or while on the go.

Data Security
Whether you’re in the office or courtroom, cloud solutions enable convenient access to your legal resources. We offer robust Security solutions to safeguard your confidential data and resources. By assessing your current security posture, we identify vulnerabilities and implement strategies to fortify your defense against cyber attacks.